Inviting and Configuring Users
Learn how to invite and configure users in Stardog Cloud.
Inviting users
To invite other users to your Stardog endpoint, click “Invite users” in the Quick Actions section of the Stardog Cloud landing page (after you have selected a connection).
From there, a box will pop up that will allow you to add users in your organization and the level of access you want to give to them.
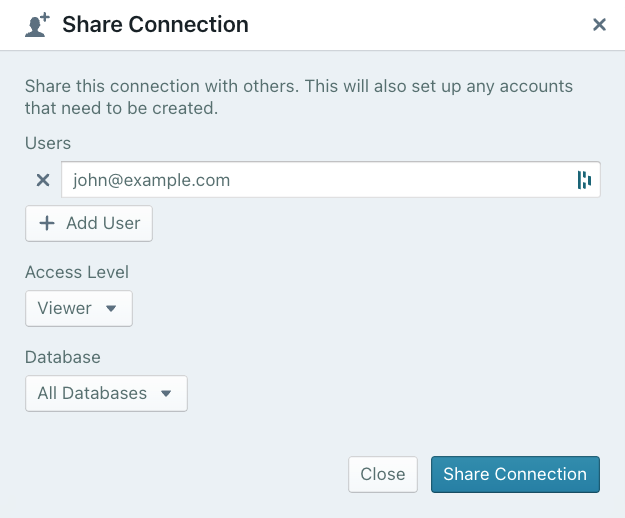
You can enter as many users as you’d like here, but they will all be given the same level of access.
There are four access level to choose from: Viewer, Collaborator, SysAdmin, and Owner. For each of those levels, you can grant access to All Databases or a specific database.
At the SysAdmin and Owner access levels, being granted access to a specific database is not substantially different than being granted access to All Databases. We recommend only granting access to All Databases at these levels.
The permissions granted to each of these four levels is below.
Viewer
All Databases
+---------------+---------------+-------------+
| Resource Type | Resource Name | Permissions |
+---------------+---------------+-------------+
| * | * | --R---- |
+---------------+---------------+-------------+
Specific database
+-----------------+---------------+-------------+
| Resource Type | Resource Name | Permissions |
+-----------------+---------------+-------------+
| db | catalog | --R---- |
| db | myDb | --R---- |
| metadata | myDb | --R---- |
| virtual-graph | * | --R---- |
| icv-constraints | myDb | --R---- |
+-----------------+---------------+-------------+
Collaborator
All Databases
+----------------------+---------------+-------------+
| Resource Type | Resource Name | Permissions |
+----------------------+---------------+-------------+
| db | * | --RW--- |
| db | catalog | --R---- |
| metadata | * | --RW--- |
| data-source | * | CDRWGKX |
| sensitive-properties | * | CDRWGKX |
| stored-query | * | CDRWGKX |
| virtual-graph | * | CDRWGKX |
| icv-constraints | * | CDRWGKX |
+----------------------+---------------+-------------+
Specific database
+----------------------+---------------+-------------+
| Resource Type | Resource Name | Permissions |
+----------------------+---------------+-------------+
| db | myDb | --RW--- |
| db | catalog | --R---- |
| metadata | myDb | --RW--- |
| data-source | * | CDRWGKX |
| sensitive-properties | * | CDRWGKX |
| stored-query | * | CDRWGKX |
| virtual-graph | * | CDRWGKX |
| icv-constraints | * | CDRWGKX |
+----------------------+---------------+-------------+
SysAdmin
All Databases
+----------------------+---------------+-------------+
| Resource Type | Resource Name | Permissions |
+----------------------+---------------+-------------+
| * | * | CDRWGKX |
| admin | * | CDRWGKX |
| db | * | --RW--- |
| db | catalog | --R---- |
| metadata | * | --RW--- |
| data-source | * | CDRWGKX |
| sensitive-properties | * | CDRWGKX |
| stored-query | * | CDRWGKX |
| virtual-graph | * | CDRWGKX |
| icv-constraints | * | CDRWGKX |
+----------------------+---------------+-------------+
It is not recommended to grant SysAdmin access to specific databases.
Owner
All Databases
+----------------------+---------------+-------------+
| Resource Type | Resource Name | Permissions |
+----------------------+---------------+-------------+
| * | * | CDRWGKX |
+----------------------+---------------+-------------+
It is not recommended to grant Owner access to specific databases.
Being granted Owner access does not make that user a superuser. See here to see how to create superusers.
User Configuration
Log into your Stardog Cloud Account and click the Stardog enpoint you wish to manage. From there, launch Stardog Studio, our Knowledge Graph IDE. With Studio you can administer your Stardog instance and create users. Your initial user will have administrative access to manage Stardog including:
- creating new users and roles
- deleting the users and roles that you have created
- creating new databases
- writing to existing databases
- deleting databases
- managing virtual graphs
- and more
Stardog uses role based access control (RBAC) similar to many traditional databases. To grant additional team members access we recommend that you provision additional users with access that is limited appropriately. For example, you could provision a new user that has the role reader (a role automatically configured by Stardog Cloud) for a new user you wish to be able to view data but not alter it.
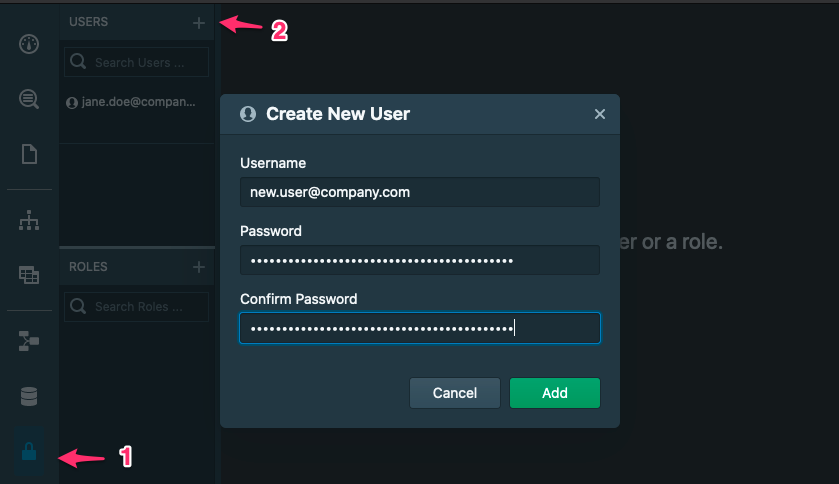
Creating a new user
Note that a Stardog user in your instance is not related to the Stardog Cloud Account used to log in to the Stardog Cloud Portal. The former authenticates a user with the instance itself, while the latter allows access to the Stardog Cloud Portal, where you can configure connections to multiple Stardog Server instances.
After creating a Stardog user with Studio, you can provide the username, password, and URL for the instance to a person who has created a Stardog Cloud Account; that person can then create a connection to the Stardog endpoint using the username, password, and URL that you provided.
We recommend that for any programmatic access to your Stardog instance you create a dedicated service account user and then limit the service account access to the minimum required by the application.
We recommend reviewing the Stardog permissions model to fully understand what is possible.
Much of the Stardog security documentation refers to configuring Stardog Server Authentication securely for on-premises deployments. With Stardog Cloud, your endpoint is configured by default to follow security best practices.